
5 key benefits of migrating SAP to Azure
December 30, 2022
Are your SAP systems and applications really secure?
March 7, 2023It´s about time for a SIEM at the SAP application level.
Many years ago I was an instructor to a group of SAP technical consultants on Security concepts around SAP and, an in that training class first thing I did was to provide each of the students with a username and password for the Windows Server Domain, as well as a SAP username and password, requesting that they had to change both passwords at first logon. They followed the instructions, logged into the Windows server domain, changed their password, then they accessed the SAP training systems and also changed their passwords. I told them to wait… In about 15 minutes I could easily hack both their domain and SAP application passwords and it was not by cheating because I had admin privileges, but using a simple brute force small program for windows, and using same SAP program that encrypt the password and make a simple comparison. Of course, that was long time ago (20 years+), and of course much has improved regarding security on Windows Servers and SAP.
However about one year and a half ago, one of our customers had their main SAP application hit by Ransomware, which got their full SAP DB encrypted and stopped their business for almost a week. Needless to say they didn’t have much security (besides backups, and also the last ones were already useless) and ended up paying the ramson. This is not very common as applying some basic and standard security policies around their networking and in their SAP applications it could have been avoided.
What it is not uncommon, and every CISO knows is that, often stealing of sensitive information comes most likely from insiders, and that in recent years more than ever before, security has become a critical aspect of protecting the information assets of enterprises against an ever increasing number, frequency and typologies of threads (for a comprehensive overview refer to the Mitre Attack Framework ).
Firewalling, DDoS protection software, antivirus and many other advanced security technologies, hardware and software have been around for a very long time. Cloud hyper-scalers vendors have been investing heavily in security features, compliance, certifications and out of the box early threat detection.
Security Information and event management systems (SIEM´s) are being increasingly adopted, and so are Security Operations Centres (SOC´s) so that early detection, investigation and response is more efficiently achieved.
While infrastructure, networking, operating systems and processes are being greatly protected, and log analysis tooling are getting increasingly intelligent, so are the threads.
SAP business applications are the core of many thousands of medium to large enterprises around the globe, and while the type of security systems and technologies mentioned above is helping, and there are many inherent security features embedded on SAP, until recently there has not been a comprehensive solution that can effectively prevent, spot, prevent and react to the threats at the application level with a high degree of intelligence and automation. SIEM systems (either on-premises or on Public Clouds) can detect and respond to threads but generally they are providing visibility mostly on the platform (infrastructure, networking, Operating system, main processes), but…. Is it enough for proactively protecting your SAP systems?. A hacker attack whether external or internal can have devastating effects on companies.
Monitoring and protecting in an automated way all aspects of security on SAP systems is not an easy task. There is a great challenge for the complexity involved and generally there is lack of knowledge and experience that combines both “standard infrastructure security” and “application security”. Complexity is due to the fact that obtaining this knowledge and experience requires a deep understanding of underlying platform and technologies, networking, general security, operating systems and SIEM, while at the same time a good level of understanding and expertise on SAP technology, architecture and applications.
At myCloudDoor we have been deploying, migrating, monitoring, supporting and automating SAP systems since 2015, and one way or another we always encountered issues related directly or indirectly with the security of those systems.
Therefore the launch of Microsoft Azure Center for SAP Solutions, and specifically Azure Sentinel for SAP is proving to be one of the most efficient tooling to protect, prevent and react quickly to internal or external threats to SAP applications with a high degree of automation and intelligence.
Microsoft Azure Sentinel is a Cloud based SIEM that can be used both for Cloud and On-premises systems: Sentinel collects events, information, detect potential vulnerability, utilizes machine learning algorithms for research and reacting on events. Sentinel includes connectors for basically all Microsoft products on Cloud, plus connectors for many of the most common third party solutions, and although it has been available for some time, it has been just recently that the connector for SAP has been released for General Availability.
Graphic below shows a schematic diagram of Sentinel for SAP
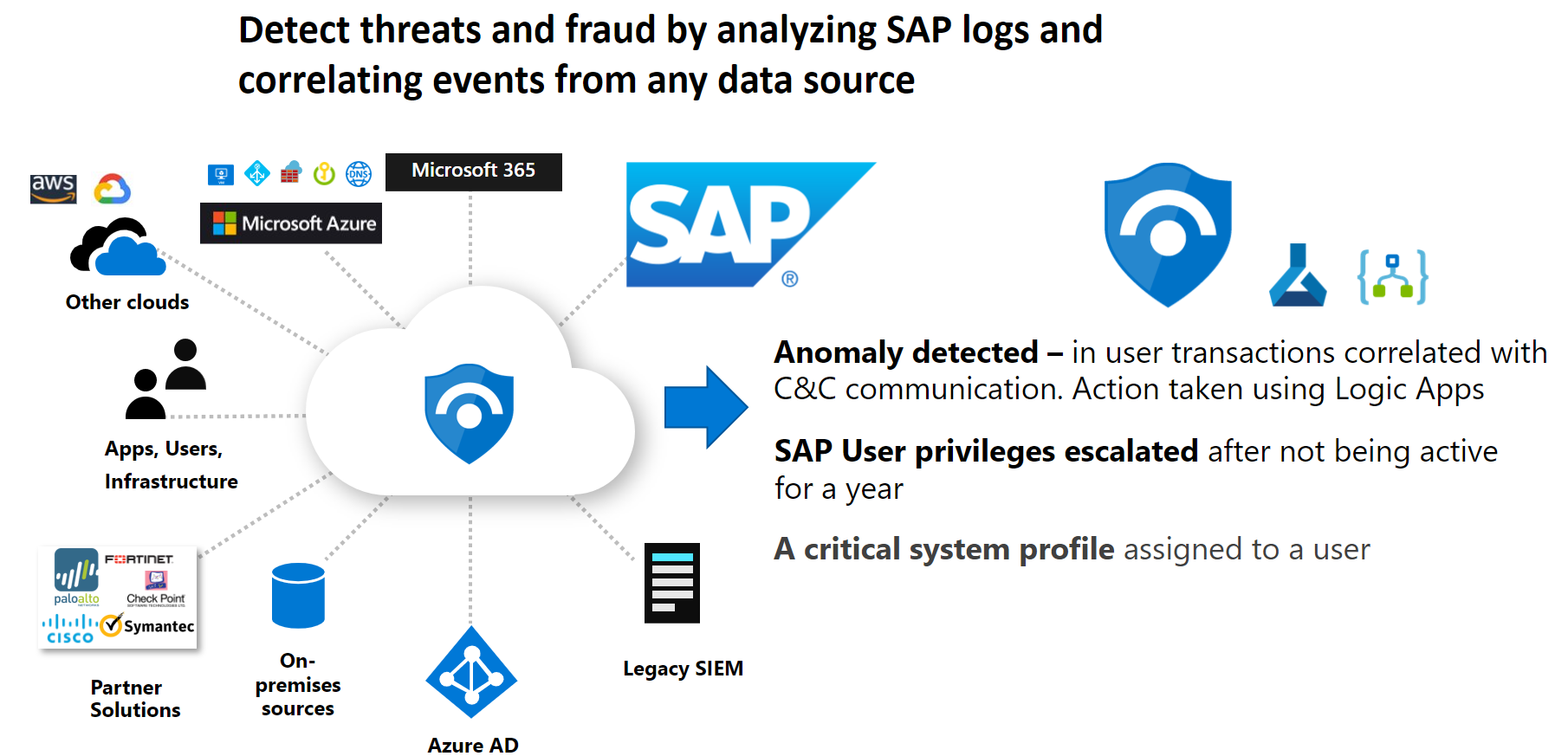
There is so much you can get out of the box and so much you can configure it is not possible to summarize in this short blog. At the end of the blog I´m including some of the main links for getting extensive and official information.
Here is a brief overview of what is Microsoft Sentinel for SAP Applications and what can achieve to take your SAP security to the highest level.
- The SAP Connector for Azure Sentinel provides with a log and data connector through a container, ingesting specific SAP logs.
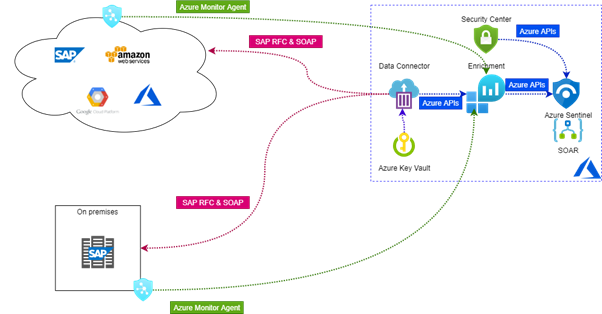
- Provides continued monitoring, thread detection, automated reactions (i.e. create alerts, connect with your ticketing systems, send events to SOC….) for your SAP applications at all levels (systems, users, programs, business processes, correlated events, database tables….).
- A collection of SAP Watchlist, including:
- SAP Systems.
- SAP Networks.
- Sensitive Data (that includes function modules, specific sensitive tables, sensitive transactions, ABAP programs…).
- User and Authorizations Watchlists (Critical Authorizations, sensitive users, sensitive roles…).
- It can detect a large variety of threats from a change on a role or privilege, to the suspicious download of a table, to the access from an unverified IP….).
- It can correlate events from SAP and other systems
- It comes with out of the box Security Content for SAP: Sentinel includes a SAP Content Hub easily deployable from the Azure portal, containing Workspaces and SAP related analytics tools. The analytics tools come with alert rules templates that can be configured on a phased way as companies start using the Sentinel for SAP capabilities.
- With all this tooling and capabilities, every customer can control and develop its own detection rules and adapt them to suit your most sensitive and valuable information within your SAP systems.
Do you need help in setting it up, getting a hands on workshop, maybe a proof of concept, help with configuration, integration with SOC or ITSM, please contact us. Discover our out of the box solutions services myCloudDoor Innovation Works – Sentinel for SAP Starter pack.
Appendix and links:
– Official full documentation of Sentinel can be found at Learn Microsoft
– A current promotion for Sentinel for SAP is running currently. More info at Azure Microsoft
– Sentinel for SAP Security Content reference (The built in workbooks, analytics rules, watchlists…) can be found at Learn Microsoft
– Deployment and configuration instructions can be found at Learn Microsoft
Jose A. Hernandez
Founder & Global CTO at myCloudDoor


